Troubleshooting Git Issues After Reinstalling Git on Windows: Ultimate Guide Step-by-Step
If you’ve been working on a project and decided to uninstall and later reinstall Git on your Windows machine(There are many reasons; mostly, we do it due to corrupted installations, upgrade issues, configuration errors, switching installation methods, or problems with path/environment variables), you might encounter some unexpected issues when trying to push or pull from your repository. These problems can include Git detecting many modified or new files, or even Git configurations being reset. Here, I will walk you through the steps to troubleshoot and resolve these problems, ensuring that your Git setup works smoothly again.
Why Problems Arise After Reinstalling Git
Uninstalling Git does not affect your existing project repositories since Git stores repository information inside each project’s .git folder. However, after reinstalling, certain configurations and settings might be different from what you had before. Here are some common reasons for issues:
- Line Ending Differences: Git’s line-ending conversion settings may have changed, causing Git to detect file modifications.
- Missing or Reset Configuration: Global Git configurations, such as username, email, or credential helper settings, might be missing or reset.
- Ignored Files: Files that were previously ignored may now appear as untracked if
.gitignorewas altered or its behavior changed. - Stale Credentials: Git might require you to re-enter your authentication details if you are using HTTPS or SSH credentials.
Let’s dive into how to resolve each of these.
Step 1: Verify Git Installation
After reinstalling Git, you should first verify whether it is installed correctly.
Run the following command in your terminal:
git --versionThis should display the current version of Git. If it returns a version number, then Git is properly installed.
Step 2: Check Your Global Git Configurations
You may need to reconfigure Git’s global settings, like your username and email. These are required when you commit to any Git repository. Check your current global Git configurations:
git config --global --listIf you don’t see your user.name or user.email, you can set them like this:
git config --global user.name "Your userName"
git config --global user.email "[email protected]"These settings are essential for Git to know who is making the commits.
Step 3: Line Ending Issues (CRLF vs. LF)
One of the most common issues after reinstalling Git is a change in how line endings are handled. Windows uses CRLF (Carriage Return and Line Feed) for new lines, while Linux and macOS use LF (Line Feed). If your project collaborates across different operating systems, Git’s line-ending conversion setting (core.autocrlf) may cause many files to appear modified after reinstalling Git.
Check Your Line Ending Settings:
To check your current line-ending conversion setting, run:
git config --global core.autocrlfThis will return one of the following values:
true: Git converts LF to CRLF when checking out code on Windows.false: Git does not change line endings.input: Git converts CRLF to LF when committing.
Set the Appropriate Line Ending Setting:
If you’re working on Windows and want to ensure consistency, it’s usually best to set core.autocrlf to true:
git config --global core.autocrlf trueOr, if you’re working on a cross-platform project, you can set it to input to avoid modifying line endings on commits:
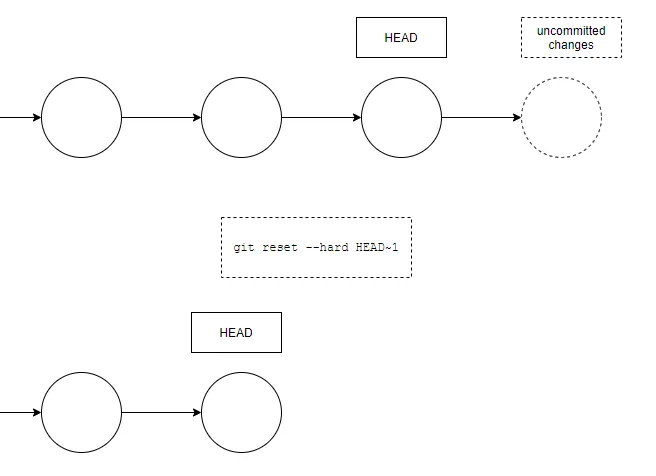
git config --global core.autocrlf inputOnce you’ve set this, reset the changes detected in your working directory:
git reset --hardThis will reset any uncommitted changes, reverting your files to the state of the last commit.
Step 4: Handling Modified and New Files
After reinstalling Git, you might see many modified or new files when you run git status, even if you didn’t actually change these files. This often happens due to changes in .gitignore or configurations.
Check .gitignore:
Ensure your .gitignore file is correctly configured. Git might now be tracking files that should be ignored. Open the .gitignore file in the root of your project directory and check whether all unwanted files or directories (e.g., logs, build files) are listed.
Run Git Check-Ignore:
To see which files should be ignored, you can use:
git check-ignore *This command will output the files that Git is ignoring. If something is missing from .gitignore, add it and then run:
git add .gitignore
git commit -m "Updated .gitignore"Step 5: Recommit or Discard Local Changes
If the changes detected by Git are legitimate, you can either commit them or discard them if they aren’t necessary.
If You Want to Keep the Changes:
If you believe the changes are valid and need to be saved, you can stage and commit them:
git add .
git commit -m "Commit changes after reinstalling Git"
git push origin master (or any current feature branch)This will save the changes and push them to the remote repository.
If You Want to Discard the Changes:
If the changes are unwanted or were caused by line-ending issues, you can discard them using:
git reset --hardThis will reset your local files to the last committed state, removing any uncommitted modifications.
Note – Even after resetting, Git is showing “untracked files” because
git reset --hardonly affects tracked files, not untracked files. Untracked files are new files that haven’t been staged or committed to the repository yet. These files remain even after a hard reset.
Why git reset --hard Leaves Untracked Files
The git reset --hard command only resets tracked files (files that are already part of the repository and have been committed). It doesn’t touch untracked files, which are new files Git hasn’t started tracking yet. If you want to make your repository completely clean (removing all untracked files as well), you’ll need to take an additional step.
Removing Untracked Files to Clean the Repository
To make the repository completely clean, you need to remove all untracked files. Here’s how you can do that:
Option 1: Use git clean
git clean is used to remove untracked files. Be very cautious when using this command, as it will delete files that are not part of the repository.
First, check what will be removed (dry run):
git clean -nIf you’re sure you want to remove those files, run:
git clean -fThis removes all untracked files. If you also want to remove untracked directories, run:
git clean -fdOption 2: Discard Only Specific Untracked Files
If there are specific untracked files you want to remove, you can manually delete them, or you can use:
git rm --cached <file>This will remove only the selected untracked file from the staging area.
Full Command to Clean the Repository
To fully clean your repository, including resetting all changes and removing untracked files, follow these commands:
Reset tracked files to the last commit:
git reset --hardClean untracked files:
git clean -fdNow, when you run git status, it should say that there’s nothing to commit, and no untracked files should be listed. Your repository will be in a clean state, just like when you cloned it or after a fresh commit.
Step 6: Reconfigure Credentials (If Necessary)
If you used HTTPS or SSH for Git authentication, you might need to re-enter your credentials after reinstalling Git. To avoid entering your username and password every time you push or pull, you can configure Git’s credential helper.
For HTTPS Authentication:
git config --global credential.helper wincredThis stores your credentials securely using the Windows Credential Manager.
For SSH Authentication:
Make sure your SSH key is correctly added. Run:
ssh-add -lIf no SSH keys are listed, you’ll need to re-add them using:
ssh-add ~/.ssh/id_rsaThe command ssh-add ~/.ssh/id_rsa is used to add a private SSH key to the SSH authentication agent (ssh-agent). Here’s a breakdown:
ssh-add: A command that adds private SSH keys tossh-agent, which manages your private keys and stores them securely in memory.~/.ssh/id_rsa: This is the path to your private SSH key (in this case, the default fileid_rsastored in the~/.sshdirectory). The~represents the home directory of the current user.
By running this command, you’re telling ssh-agent to hold the private key in memory, allowing you to authenticate with SSH servers without needing to enter your passphrase for each connection.
Note – If your SSH key was reset, you may need to regenerate it and add it to your Git hosting service (GitHub, Bitbucket, etc.).
Conclusion
Reinstalling Git on your Windows machine can sometimes lead to unexpected behavior in your repositories, such as detecting modified files, resetting configurations, or needing to reconfigure credentials. By following the steps outlined above, you can troubleshoot and resolve these issues to get Git working smoothly again.
Remember to verify your Git installation, check your global configuration, review line-ending settings, and ensure that ignored files are still ignored. In most cases, resetting line-ending settings and recommitting or discarding changes will solve the issue.
By taking these steps, you can confidently continue working with Git after reinstalling it on your machine, without losing any data or productivity.
Happy committing..!